Universities and colleges today operate in a fully digital academic environment online classes, LMS platforms, cloud storage, digital fee payments, and constant email communication. While this digital shift has improved accessibility and efficiency, it has also opened the door to a surge in phishing attacks targeting students, faculty, and administrative staff.
Phishing is no longer limited to generic scam emails. Modern attackers deliberately craft messages that imitate university communication with astonishing accuracy, fake exam timetables, fraudulent fee reminders, cloned login pages, scholarship alerts, job offers, and IT helpdesk notices. Because these emails look familiar and urgent, they spread quickly through campus inboxes and often go unnoticed until the damage is done.
This growing threat has made one reality clear: phishing awareness cannot be limited to IT teams alone. It must be campus-wide. Every student, every lecturer, every researcher, and every staff member plays a critical role in preventing cyber incidents. Without institution-wide awareness, even a single compromised account can lead to financial loss, data breaches, academic disruption, and significant reputational damage.
The Growing Threat of Phishing in Modern Campuses
Phishing has become one of the most persistent and damaging threats facing modern universities and colleges. As campuses continue to digitalise learning, communication, and administration, attackers are finding new ways to blend malicious emails into everyday academic life. What once looked like an obvious scam now appears as a routine message from a lecturer, department, or university system, making phishing attacks harder to detect and far more dangerous.
1. Increasing Sophistication of Attacks
Phishing attacks targeting universities have evolved dramatically. Cybercriminals now mimic university branding, communication styles, and academic workflows with alarming accuracy. Fake exam updates, cloned LMS login pages, fraudulent fee reminders, and internship scams are crafted to look identical to real campus communication. This level of sophistication makes it difficult for students and staff to distinguish genuine messages from malicious ones.
2. High Volume of Digital Communication
Students and staff receive an overwhelming number of emails every day, from academic updates and assignments to administrative notices and event reminders. In this crowded digital environment, malicious emails easily blend in. Because users are constantly scanning and responding to messages, attackers rely on hurried decision-making to trick recipients into clicking harmful links.
3. Decentralised Academic Environments
Modern universities operate like mini-cities, with multiple faculties, departments, and administrative units—all using different communication formats. This lack of uniformity gives attackers an advantage. By copying department-specific styles or impersonating familiar staff members, cybercriminals can make phishing emails appear legitimate and trustworthy.
4. Expanded Attack Surface Through Remote & Hybrid Learning
With students and staff accessing systems from home networks, public Wi-Fi, personal devices, and mobile phones, the attack surface has widened considerably. These environments are less secure than campus networks, making it easier for attackers to exploit weakened defences.
5. Attackers Exploit Academic Pressure and Timing
Cybercriminals strategically launch phishing campaigns during high-stress periods such as exams, assignment deadlines, and fee payment cycles. During these times, users are more likely to act quickly, overlook warning signs, and click without verifying. Attackers understand this behaviour and use it to increase their success rate.
Common Phishing Tactics Used Against Universities
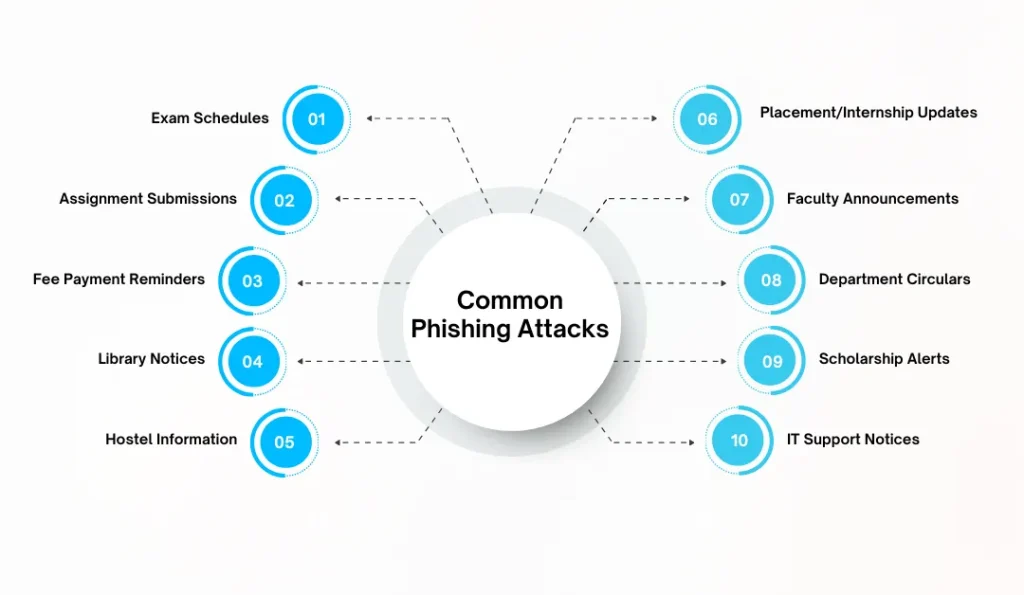
Phishing attacks targeting universities are becoming increasingly deceptive, blending seamlessly into the daily flow of academic communication. Because students, faculty, and staff regularly receive emails about exams, assignments, fees, events, and campus updates, attackers use this familiarity to disguise malicious messages as routine university notices. By mimicking trusted departments, copying official templates, and leveraging urgent academic scenarios, cybercriminals trick users into clicking harmful links or revealing sensitive information. Understanding these common phishing tactics is the first step toward preventing them.
1. Exam Schedules
Attackers send fake emails claiming to share urgent exam updates or revised timetables. Students click quickly under pressure, making this a highly effective scam.
2. Assignment Submissions
Cybercriminals impersonate professors or LMS platforms, sending fake submission links. When students log in, attackers steal their credentials.
3. Fee Payment Reminders
Scammers send fraudulent notices demanding immediate tuition or fee payments. The links often lead to fake payment portals designed to capture bank or card details.
4. Library Notices
Fake emails about overdue books, expiring access, or new digital resources are used to lure users into entering their login details on cloned library portals.
5. Hostel Information
Students receive false alerts about room allotments, maintenance updates, or hostel fee notices. These emails often contain malicious links or attachments.
6. Placement / Internship Updates
Cybercriminals impersonate the Careers Team or employers, offering attractive internships or part-time jobs to steal personal or academic information.
7. Faculty Announcements
Scammers pose as lecturers or department heads to send fake academic updates, meeting links, or material downloads—making recipients trust the message instantly.
8. Department Circulars
These look like official notices about schedule changes, workshops, or new policies. Attachments or links typically contain malware or credential-harvesting sites.
9. Scholarship Alerts
Fake scholarship approvals or renewal notices trick students into entering sensitive information or paying “processing fees.”
10. IT Support Notices
Phishers impersonate the university’s IT team, warning users about password expiry, storage limits, or account suspension, leading them to fake login pages.
Consequences of Falling for Phishing Attacks
Phishing attacks may start with a single deceptive email, but their impact can quickly spread across an entire university or college. When even one student, staff member, or faculty member falls for a malicious message, the consequences can be far-reaching, costly, and difficult to contain.
1. Financial Loss
Phishing often leads to direct financial damage—such as stolen tuition payments, fraudulent bank transactions, or payroll redirection. Attackers also exploit administrative staff to initiate fake invoice payments or wire transfers, resulting in major institutional losses.
2. Data Breaches
University accounts store sensitive information: personal details, academic records, research data, payroll information, and more. A compromised account can expose this data to attackers, leading to identity theft, leaked research, and stolen intellectual property.
3. Operational Disruptions
Phishing incidents can shut down essential campus systems. Hackers may gain access to LMS platforms, email servers, or internal networks, causing class cancellations, website outages, or widespread IT downtime. In severe cases, phishing leads to ransomware attacks that freeze entire operations.
4. Reputational Damage
When a university suffers a phishing-related breach, trust erodes quickly. Students, parents, faculty, partners, and research collaborators may question the institution’s ability to safeguard data. Reputational harm can impact admissions, partnerships, funding, and long-term credibility.
5. Compromised Research and Intellectual Property
Many universities lead critical research, innovation, and industry projects. A single compromised account can expose confidential findings or give attackers access to sensitive research data, putting years of work at risk.
6. Widespread Account Takeover
Phishing attacks often spread by using compromised accounts to target others within the institution. Once attackers gain access to one inbox, they can impersonate the victim to send more phishing emails, escalating the attack across departments or entire faculties.
How PhishCare Strengthens Phishing Awareness?
PhishCare is designed specifically to help universities and colleges build a cyber-aware community that can identify, report, and respond to phishing threats before they cause harm. By combining realistic simulations, instant learning, and powerful analytics, PhishCare transforms security awareness from a one-time activity into an ongoing culture of vigilance.
1. Realistic Academic-Themed Simulations
PhishCare sends highly contextual phishing simulations that mirror the exact types of emails students and staff encounter daily—exam updates, assignment reminders, scholarship alerts, fee notices, IT support messages, and internship offers. These realistic campaigns create genuine teachable moments by exposing users to the threats they are most likely to face.
2. Instant Awareness Lessons After Clicks
Whenever a user interacts with a simulated phishing email, PhishCare immediately redirects them to a short, visual awareness module. This micro-training explains what made the email suspicious, which red flags were missed, and how to avoid similar scams in the future. Learning happens in real time, making it far more memorable and effective.
Why PhishCare is the Best Phishing Simulation and Cyber Security Awareness Training Tool

- Customizable Templates
- Awareness Module
- Assessment Test
- Comprehensive Tracking
- Graphical Dashboard Access
- Campaign Report
- Custom Domain Integration
3. Advanced Analytics to Identify High-Risk Users
PhishCare provides institutions with deep visibility into how every department or user group responds to simulations. Universities can track who clicked, who reported, who submitted credentials, which departments struggle most, and which phishing themes are most effective. These data-driven insights enable targeted training where it’s needed most.
4. Scalable for Institutions of All Sizes
Whether a campus has 800 students or 80,000, PhishCare scales effortlessly. It supports multi-campus universities, remote-learning environments, polytechnics, vocational institutes, and large academic networks. Automated delivery and reporting make it easy for small IT teams to manage institution-wide campaigns.
5. Builds a Culture of Reporting and Vigilance
By repeatedly training users to recognise suspicious emails and offering easy reporting tools, PhishCare strengthens the culture of cybersecurity across the entire campus. Over time, students and staff become more proactive, more cautious, and more confident in identifying risks, turning the human layer from the weakest link into the strongest defence.
Moving Toward a Cyber-Aware Campus Community
Phishing attacks are no longer isolated incidents but a continuous threat targeting every corner of modern universities and colleges. As academic environments become more digital and interconnected, the responsibility for cybersecurity extends beyond IT teams to every individual on campus.
Building strong phishing awareness across the university ecosystem, students, lecturers, researchers, and administrative staff, is one of the most effective ways to reduce risk. When people understand how phishing works, recognise red flags, and know how to report suspicious emails, the entire institution becomes more resilient.
PhishCare plays a central role in making this possible. Through realistic simulations, instant awareness lessons, and deep behavioural analytics, it equips campuses with the tools they need to strengthen human defences where attackers strike most often.
FAQs
1. Why are universities such common targets for phishing attacks?
Universities store large amounts of personal data, financial information, academic records, and research materials. Their open, decentralised structure and heavy reliance on email communication make them vulnerable to attackers who impersonate trusted departments or staff.
2. What should someone do immediately after clicking a phishing link?
They should stop entering any information, change their university account password, enable multi-factor authentication if available, and report the incident to the IT or cybersecurity team immediately.
3. Are students more vulnerable than faculty and staff?
Students often have less cybersecurity training and face constant academic pressure, making them more susceptible. However, faculty and administrative staff handle sensitive data and are equally high-value targets for attackers.
4. How often should universities run phishing simulations?
Monthly or quarterly simulations are recommended to keep awareness high, reinforce safe behaviours, and measure improvement over time.
5. How does PhishCare help reduce phishing risks?
PhishCare delivers realistic academic-themed phishing simulations, instant awareness training, and detailed analytics. It helps universities identify high-risk users, improve reporting culture, and strengthen campus-wide security behaviours.
6. Is PhishCare suitable for small colleges as well as large universities?
Absolutely. PhishCare scales seamlessly and supports institutions of all sizes—from small vocational colleges to large multi-campus universities.