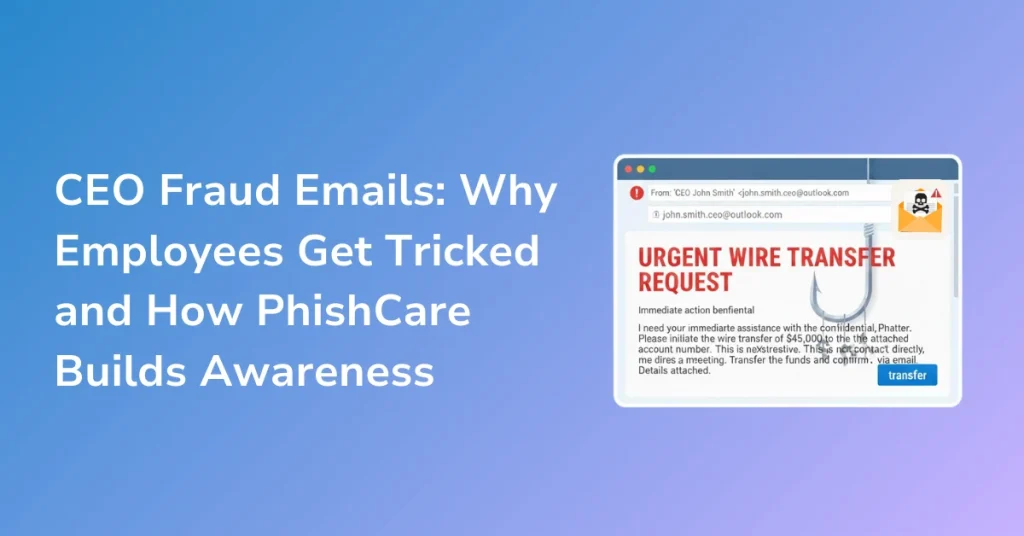
CEO fraud emails have become one of the most costly and effective forms of cybercrime impacting organizations worldwide. Unlike traditional phishing attacks that rely on malicious links or obvious red flags, CEO fraud focuses on manipulating human behavior. These emails impersonate senior leadership and request urgent actions such as transferring funds, sharing confidential information, or bypassing established approval processes.
Over the past few years, CEO fraud has shifted from being an occasional threat to a persistent business risk. This shift explains why organizations are increasingly asking a critical question: why do employees keep getting tricked, and how can awareness training actually reduce this risk? This is where PhishCare plays an important role by addressing the human decision-making layer that technical tools alone cannot fully protect.
What Are CEO Fraud Emails and Why Are They Increasing
CEO fraud, often categorized under business email compromise, occurs when attackers impersonate senior executives such as the CEO, CFO, or managing director. These emails usually avoid links or attachments, making them difficult for traditional email security filters to detect.
Over the last five years, global cybersecurity reports have consistently highlighted business email compromise as one of the top causes of financial cyber loss. Reported figures show that billions of dollars have been lost globally due to CEO fraud and related email scams, with year-on-year growth reflecting how effective these attacks remain.
One key trend is that attackers now invest time studying organizations. They analyze LinkedIn profiles, corporate websites, press releases, and social media to understand reporting hierarchies and executive communication styles. This preparation makes CEO fraud emails highly convincing and difficult to distinguish from legitimate messages.
Why Employees Get Tricked by CEO Fraud Emails
Employees do not fall for CEO fraud because they lack intelligence or training. They fall for it because these attacks exploit normal workplace behavior.
Authority plays a significant role. When an email appears to come from the CEO, employees feel pressure to comply quickly. Questioning leadership can feel inappropriate, especially in hierarchical organizations.
Urgency is another powerful factor. CEO fraud emails often include phrases that suggest confidentiality or immediate action, leaving little time for verification. During busy workdays, employees are more likely to respond without pausing.
Familiarity also matters. CEO fraud emails are typically short, direct, and similar to how executives actually communicate. There are no spelling mistakes, suspicious URLs, or visible malware. To the recipient, nothing looks technically wrong.
These psychological triggers explain why policy documents and generic awareness emails alone rarely prevent CEO fraud incidents.
Why Traditional Security Training Is Not Enough
Most cybersecurity awareness programs focus on identifying phishing links, attachments, or obvious anomalies. CEO fraud attacks deliberately avoid these indicators. This creates a knowledge gap where employees believe they are trained, yet still fall victim when faced with a realistic executive request.
Another limitation is that traditional training is passive. Employees are told what to watch out for but are never placed in realistic, pressure-driven scenarios. When the real email arrives, they experience the stress and urgency for the first time. For CEO fraud prevention, awareness must be experiential, not theoretical.
The Role of Awareness Training in Preventing CEO Fraud
Effective protection against CEO fraud starts with changing employee behavior. Employees need to learn when to pause, how to verify unusual requests, and when to escalate rather than comply.
This is where PhishCare adds value. PhishCare does not stop emails from reaching inboxes. Instead, it trains employees through realistic simulations and targeted awareness lessons.
Employees receive simulated CEO fraud emails that mirror real-world attacks. These simulations include urgent payment requests, confidentiality cues, and authority-driven language. When employees react incorrectly, they are immediately guided through short awareness modules explaining the warning signs they missed. This method helps employees build instinctive caution rather than relying on memory alone.
Why PhishCare is the Best Phishing Simulation Tool and Security Awareness Training for Employees

- Customizable Templates
- Awareness Module
- Assessment Test
- Comprehensive Tracking
- Graphical Dashboard Access
- Campaign Report
- Custom Domain Integration
How CEO Fraud Simulations Improve Decision Making
CEO fraud simulations focus on the human decision moment. There is often no link to click and no obvious technical clue. The choice lies entirely in whether the employee decides to trust, verify, or escalate.
Repeated exposure to these scenarios teaches employees that it is acceptable and encouraged to verify unusual executive requests. Over time, this creates a culture where security checks are seen as responsible behavior rather than hesitation.
Organizations that implement simulation-based awareness report reduced risky actions, improved verification habits, and increased internal reporting of suspicious executive emails.
Who Is Most at Risk From CEO Fraud
While finance and HR teams are commonly targeted, CEO fraud attacks increasingly reach a broader group of employees. Operations teams, executive assistants, procurement staff, and even junior employees may be targeted if attackers believe they can influence internal processes. This is why CEO fraud awareness must be organization-wide and not limited to specific departments. PhishCare allows organizations to run role-based simulations, helping employees understand how CEO fraud could target their specific position.
The Business Impact of CEO Fraud
CEO fraud incidents often result in direct financial losses, but the damage goes further. Organizations may face regulatory scrutiny, audit issues, reputational harm, and internal trust breakdowns.
Industry analyses over the last few years show that organizations that invest in continuous awareness training experience significantly lower incident rates compared to those relying only on policies and technical controls. This reinforces the idea that awareness is a measurable defense mechanism, not just an educational exercise.
Awareness Is the Only Sustainable Defense Against CEO Fraud
CEO fraud emails continue to succeed because they target human behavior rather than technical weaknesses. Attackers will keep refining these methods because they work. While no awareness platform can stop every fraudulent email from arriving, training can stop employees from acting on them.
PhishCare by CyberSapiens addresses this challenge by placing employees in realistic scenarios that build confidence, caution, and verification habits. Through repetition and immediate learning, employees become more comfortable questioning authority-based requests and following secure processes. For organizations looking to reduce financial risk and strengthen internal decision-making, building awareness around CEO fraud is not optional. It is a necessity.
FAQs
1. What exactly are CEO fraud emails?
CEO fraud emails are a form of business email compromise where attackers impersonate senior executives such as the CEO or CFO. These emails usually request urgent or confidential actions like transferring money, sharing sensitive data, or bypassing approval processes. They rely on authority and urgency rather than technical exploits.
2. Why do employees fall for CEO fraud emails even when they are experienced?
Employees fall for CEO fraud emails because the attacks exploit workplace psychology. The message appears to come from leadership, creates urgency, and often mirrors real executive communication styles. Even trained employees can react automatically under pressure if they have never experienced a realistic scenario before.
3. Can email security tools block CEO fraud emails?
Not always. Many CEO fraud emails contain no malicious links or attachments, which allows them to bypass traditional email filters. This is why technical controls alone are insufficient and must be supported by strong awareness training.
4. How does PhishCare help reduce CEO fraud risk?
PhishCare helps reduce CEO fraud risk by training employees through realistic simulations and short awareness lessons. It does not block emails. Instead, it teaches employees how to recognize suspicious executive requests and verify them safely before taking action.
5. What kind of CEO fraud scenarios does PhishCare simulate?
PhishCare simulates scenarios such as urgent fund transfer requests, confidential data sharing emails, gift card purchase requests, and messages that ask employees to bypass internal approval workflows. These simulations closely resemble real CEO fraud attacks seen across industries.