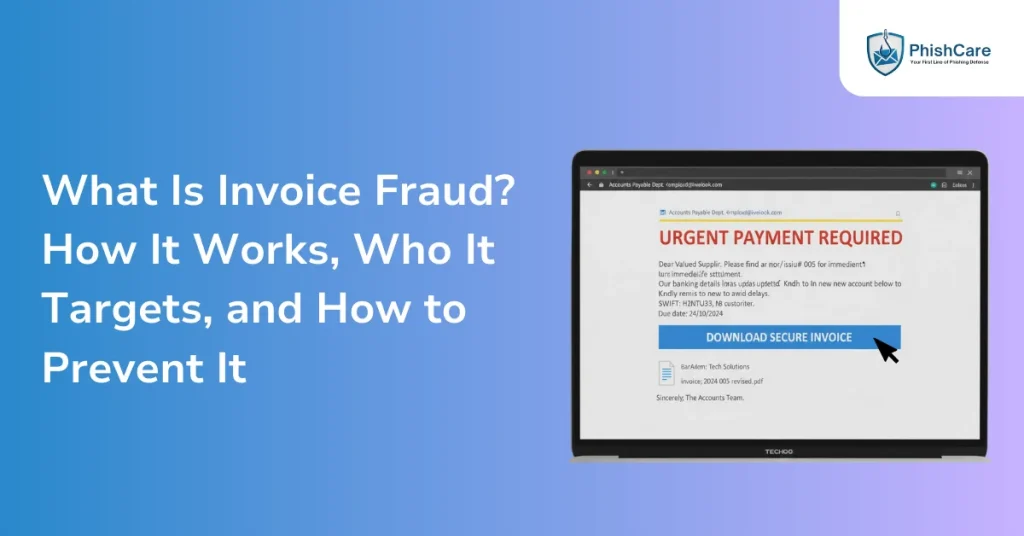
Invoice fraud, also known as mandate fraud or vendor payment fraud, is a form of business email compromise where criminals trick organisations into paying money to a fraudulent bank account. The attacker either sends a completely fake invoice pretending to be a legitimate supplier or intercepts a real invoice and alters the payment details before forwarding it to the victim organisation.
In many cases, the fraud is only discovered weeks later when the genuine supplier follows up for payment. By that time, the funds have often already been withdrawn, laundered, or transferred across multiple accounts.
Invoice fraud is one of the most financially damaging cyber scams affecting businesses today. According to the FBI’s Internet Crime Report, business email compromise, including invoice fraud, caused over $2.4 billion in reported losses in 2021 alone, with an average loss exceeding $120,000 per incident.
How Invoice Fraud Works in Real Business Environments
The Anatomy of a Typical Invoice Fraud Attack
Invoice fraud is rarely random. It is usually targeted, researched, and carefully executed using social engineering rather than technical exploits. A common real-world example looks like this:
A legitimate supplier sends a genuine invoice for $15,000. A hacker intercepts that email, replaces the bank account details with their own, and forwards the altered invoice to the accounts team. The payment is processed, and only later does the real supplier report non-payment.
In another scenario, the attacker directly impersonates a supplier and claims that their banking details have changed due to an audit, merger, or internal policy update. Urgency is emphasized so the payment is updated without verification.
Common Techniques Used in Invoice Fraud Attacks
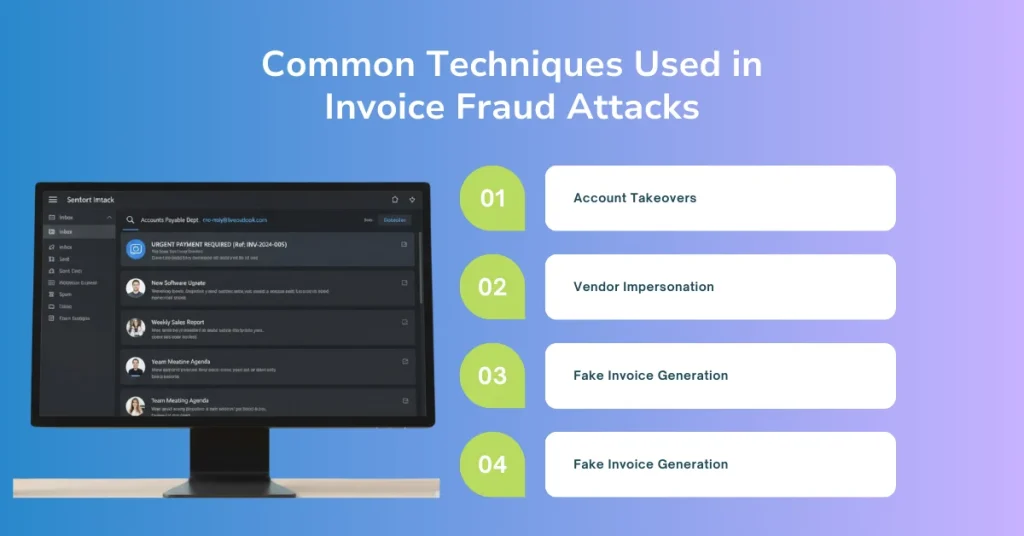
1. Account Takeovers
Attackers compromise a real employee email account, often within finance or procurement. Once inside, they monitor invoice conversations and inject fraudulent instructions at the right moment.
2. Vendor Impersonation
Fake domains are created that look almost identical to real supplier domains. For example,
vendor@abc.com becomes vendor@abc-finance.com.
Invoices sent from these look authentic to busy accounting staff.
3. Fake Invoice Generation
Attackers replicate real vendor branding, signatures, formatting, and language to make fraudulent invoices appear legitimate.
4. Employee-Driven Fraud
In some cases, internal staff may abuse their access to create or approve fraudulent invoices, either independently or in coordination with external attackers.
Who Are the Biggest Targets of Invoice Fraud Inside Companies
Invoice fraud does not target IT teams first. It targets financial authority and payment workflow owners.
1. Accounts Payable and Finance Teams
These professionals process high volumes of invoices under time pressure. Attackers exploit workload, deadlines, and routine payment cycles.
2. Procurement and Vendor Management Teams
They maintain supplier relationships and are often the first point of invoice contact.
3. CFOs and Finance Managers
Senior finance leaders are targeted using impersonation and urgent payment requests tied to confidential transactions.
4. Operations and Project Managers
They authorize payments linked to projects and vendor deliverables.
5. Executives and Business Owners
Smaller organizations often lack segregation of duties, making owners and founders prime targets.
Why Invoice Fraud Is So Hard for Traditional Security to Stop
Unlike malware-based attacks, invoice fraud emails often contain:
- No malicious links
- No infected attachments
- No obvious technical red flags
Because the email appears legitimate and contextual, traditional secure email gateways frequently allow it through. Detection depends almost entirely on human judgment. This is why awareness and simulation-based training are now considered essential for invoice fraud prevention.
How PhishCare Helps Organizations Detect and Resist Invoice Fraud
PhishCare helps organizations prepare specifically for invoice fraud through realistic phishing simulations and behaviour-driven awareness training.
PhishCare allows organizations to:
- Simulate vendor impersonation attacks
- Test employee responses to urgent payment requests
- Measure who verifies, who reports, and who proceeds with payment
- Identify departments most vulnerable to invoice fraud
- Deliver immediate awareness feedback after simulation errors
PhishCare does not block invoice fraud emails. Instead, it trains employees to recognize and respond correctly once a fraudulent invoice reaches the inbox.
Why PhishCare is the Best Phishing Simulation and Cyber Security Awareness Training Tool

- Customizable Templates
- Awareness Module
- Assessment Test
- Comprehensive Tracking
- Graphical Dashboard Access
- Campaign Report
- Custom Domain Integration
How to Prevent Invoice Fraud in Organizations
1. Verification and Payment Controls
Invoices must always be cross-checked against purchase orders and verified against existing supplier records. Any request to change banking details must be treated as high-risk.
2. Verbal Confirmation
Requests for payment changes must be confirmed using trusted phone numbers on record, never from details inside the email.
3. Dual Authorisation
Different individuals should verify and release payments to reduce single-person risk.
4. Supplier Contact Governance
Dedicated points of contact should be assigned for regular vendors to avoid confusion.
5. Staff Awareness Training
Teams that handle invoices must be trained to recognise social engineering, urgency tactics, and impersonation behaviour. Simulation-based awareness through platforms like PhishCare significantly reduces real-world success rates.
What to Do If Your Organisation Becomes a Victim of Invoice Fraud
If invoice fraud is suspected:
- Act immediately and contact your bank
- Initiate a payment recall
- Preserve all email evidence
- Inform internal compliance and legal teams
- File a cybercrime and financial fraud report
This delays significantly reduce the likelihood of fund recovery.
Why Invoice Fraud Is Also a Supply Chain Risk
Invoice fraud rarely affects just one company. It can disrupt:
- Cash flow
- Vendor trust
- Contractual relationships
- Business credit positions
Organisations should actively share fraud awareness with suppliers and encourage cyber hygiene across the supply chain. Regular vendor cybersecurity verification and lifecycle risk assessments are now considered a financial best practice.
Why Awareness-Driven Defense Is the Only Long-Term Solution
Invoice fraud thrives on urgency, authority, and routine behaviour. The only sustainable defence is building a workforce that:
- Pauses before updating payment details
- Verifies before transferring funds
- Reports suspicious requests immediately
Simulation-driven awareness platforms like PhishCare by CyberSapiens convert this behaviour into daily practice rather than theoretical policy.
Invoice Fraud Is a Financial Attack, Not Just a Cyber Incident
Invoice fraud directly targets organizational revenue, not just data. A single successful invoice scam can wipe out months of profit, strain vendor relationships, trigger regulatory review, and erode stakeholder confidence.
Because most invoice fraud attacks bypass technical security controls, prevention depends on human verification behavior. Through structured phishing simulations, reporting analysis, and targeted training, platforms like PhishCare allow organizations to measure real risk, reinforce correct behavior, and prevent high-impact financial loss before it occurs.
FAQs
1. What is invoice fraud in simple terms?
Invoice fraud is when criminals trick businesses into paying a fake invoice or diverting a real payment to a fraudulent bank account by impersonating a supplier.
2. Why is invoice fraud so difficult to detect?
Because emails often appear legitimate and contain no malware or suspicious links, detection depends entirely on employee verification behavior.
3. Who is most vulnerable to invoice fraud in companies?
Accounts payable teams, procurement staff, finance managers, CFOs, and business owners are the most targeted.
4. How does PhishCare help prevent invoice fraud?
PhishCare runs realistic vendor impersonation simulations and trains employees to verify, report, and resist fraudulent payment requests.
5. Can banks always recover money lost to invoice fraud?
No. Recovery depends on how fast the fraud is reported. Delays drastically reduce the chance of reimbursement.